TL;DR
Administrator's Web Console of Apache ActiveMQ versions 5.0.0 - 5.13.0 were vulnerable to several attacks, exploiting which unauthenticated client (i.e. accessing open STOMP port) could remotely receive Administrator’s password in plaintext and thus access all ActiveMQ data, such as queues, topics and messages.
Typical attack scenario:
a) Attacker creates a new message queue and drops a message into it, in order to exploit Stored XSS in queue name. It is even possible to email administrator with a fully prepared link with XSS.
b) When administrator accesses the page, his browser is hooked – it accesses Attacker’s server in order to receive commands in background.
c) Using XSS, it is possible to download all data from destination server, such as queues, topics, messages, etc.
d) But what is more interesting – using XSS, we can access Jolokia API. Using this API, it is possible to
(1) Obtain Full Path through accessing /api/jolokia/read/java.lang:type=Runtime/ClassPath page;
(2) Call Java Garbage Collector in order to remove unnecessary objects from memory;
(3) make Heap Dump and put this file into webapps directory so it can be accessed from Web, as far as we know Full Path.
e) By parsing Heap Dump file with regexp, it is possible to find Authorization: Basic string, which remains in memory as a part of HTTP packet, which contains administrator’s password in base64.
Demo:
Download attacker's server files. <- clickable
Vendor announcement: https://activemq.apache.org/security-advisories.data/CVE-2016-0782-announcement.txt
Description of all XSS issues:
[Unauthenticated User] tag here means that any user can reproduce this bug, using connect to default STOMP port.
1.
Vulnerability: Full Java Memory Dump can be stored to any folder on server.
POST data: { "type":"EXEC", "mbean":"com.sun.management:type=HotSpotDiagnostic", "operation":"dumpHeap", "arguments":["FULL_PATH",0]}
2.
Vulnerability: [Unauthenticated User] Stored XSS.
Vulnerable parameter: Queue name.
Step 1: Add new queue with vector "><svg/onload=alert(1)>
Step 2: Push a new message into this queue.
Step 3: Access this message using ActiveMQ
Web Console. Alert will pop up.
3.
Vulnerability: [Unauthenticated User] Stored XML-XSS
It is necessary to create new queue with
name:
1"><x:script xmlns:x="http://www.w3.org/1999/xhtml">alert('xss');</x:script>
Vector will be executed on page http://0.0.0.0:8161/admin/xml/queues.jsp
4.
Vulnerability: [Unauthenticated User] Stored XSS
Attacker should launch “consumer” script in
order to receive messages from queue/topic with XSS in name:
In administrator panel, a new connection will
appear in Connections tab (in case of receiving messages from topic - also in
Subscribers tab). After clicking "connection" link (in order to
access page with details about the connection), XSS alert will pop up:
5.
Vulnerability: [Unauthenticated User; User Interaction Required] Stored XSS
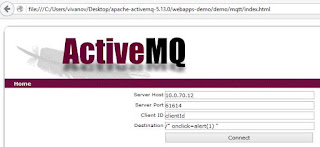
In this case, I used Demo-Example to emulate
connection: /apache-activemq-5.13.0/webapps-demo/demo/mqtt/index.html :
Step 1: Demo-Example connects to server using
ws:// protocol. A new connection in Connections tab (Admin Web Console) will
appear.
Step 2: By clicking on the connection link,
you can see a link to Destination ("Topic" - in my case).
Step 3: Symbol > is filtered, so attacker
can only write additional tag attribute such as "onclick". So in my
example, XSS will be launched by clicking crafted link.
6.
Vulnerability: [Self-XSS; I did not find a way to insert new subscriber by
Unauthenticated user – it may be possible] Stored XML-XSS.
Step 1: Add new subscriber. Vulnerable
parameters: Topic Name, Subscriber Name. Vector:
1"><x:script xmlns:x="http://www.w3.org/1999/xhtml">alert('xss');</x:script>
Step 2: XSS will be displayed on page http://0.0.0.0:8161/admin/xml/subscribers.jsp
- similar to XSS #2.







No comments:
Post a Comment